I recently received a notice from my kid's after-school care provider that they had setup an online service to check on the bill and update personal information, etc. Well, that's nice — I thought — so I hopped right on setup the account.
At first, some good signs. All the accounts were pre-setup with the registered email and a password was pre-set that was based on some information most people wouldn't have. Not perfect, but better than most.
However, when I tried to login I was mis-generating the password (four digit year instead of two) so I gave up and hit the "Forgot Password" link to setup the account that way.
This, folks, is where I started to get a little concerned.
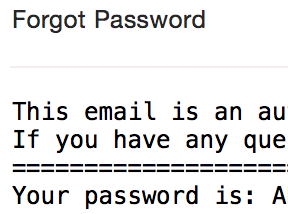
Yes, that's not only the real password sent over email, but a clever person will pause and say, "Wait, the password is recoverable?"
It would appear so. Passwords are stored in a recoverable way and regularly emailed in plain text to people rather than having a reset system.
That terrifying moment behind me (and knowing that I simply had to use a unique password on this site), I used 1Password's generator to make a good password. Well, there's problem two.

The passwords, which are recoverable, are limited to 10 characters or less. Oh, and there are also no length or complexity requirements. My password could be "x" and be valid.
On the one hand, that does increase the number of possible permutations (something I advocate for) but it also lets idiots be idiots (something I don't advocate for). In any case, the site where my kid's registration information resides is eminently hackable.
I know what you're thinking. Surely, if there's any sense in the world, they at least got the most basic, trivial thing right when it comes to safeguarding personal information on the web? You'd be wrong.
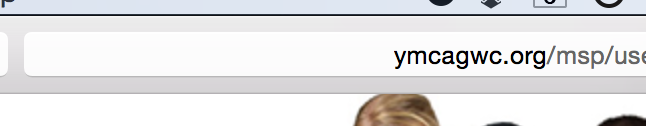
That's right. No SSL. At all.
The only word for this is irresponsible. When they get hacked and my information is out in the world there will be no amount of spin that will give me a moment's pause in putting all the blame completely on their system design, of which every component is in blatant violation of their declared security practices.
A series of events unfolded recently that led me to reconsider a lot about my digital life. The short story — and there is a long one — is that my home was broken into and my computers were stolen. The thieves also managed to take some accessories and drives but, astonishingly, left my Time Machine drives for the two computers. While it’s bad, it could have been so much worse.
Let’s start with the bad, then. My tax return was on the desktop of the desktop. My social, income, my son’s social, and the 8332 with the ex’s social were all inside a regular PDF file on the desktop. Oh, and my credit reports as I’d just gotten my yearly copies. If they dig around a little they’ll come across lots of proprietary source code (at least that’s on an encrypted disk image with no stored password in the keychain).
Then the worse: the computer was set to automatically login and neither the user nor the partition were encrypted. Further, the keychain was — as is the default — set to automatically unlock on login. So if you turned the computer on, you could log in to anything I used without a barrier.
I won’t mince words here: that was just stupid of me. It’s why I’ve decided to change everything about how I live digitally. Hopefully my lessons will serve as warnings to others.
The Good
I have renter’s insurance. Again, I’ll be frank: it wasn’t my idea. My apartment complex requires it (and more are) so I got it. My agent gave me a short talk about the Replacement Coverage option and about how, if I have computers, that’s going to save my bacon someday for the measly addition of $30 to the yearly price.
It saved my bacon.
The computers were old (about five years old) and the depreciation table has computers down for a six year life. What this means is that a computer purchased for $1,000 will lose $166.67 of value every year. Without the additional coverage I would have been handed a check for about one sixth of the original value for the equipment and bid a swell day (which it completely would not have been). With the coverage, however, I’m given that check first and then told to show receipts for replacing the equipment at modern prices and they’ll issue additional checks to cover the difference.
My 2008 iMac, MacBook Pro, and Cinema Display have thus morphed into a MacBook Pro (Retina) and Thunderbolt Display (I have two years to buy the iMac and don’t need it right now, so I’ll wait a little for a refresh). The original MBP was mid-line with some additions and that translated to the top-of-the-line MBP with no additions as far as placement on the scale is concerned. Apple sells no other Apple-branded displays than the Thunderbolt at the moment. They even tossed in a Superdrive since Apple killed the optical in that model (so it would be a feature-for-feature replacement). The experience of using my computer instantly went from The Virgin Suicides to Amelie.
Lesson: Get replacement coverage. It was the one thing I did right.
Backing Up
First and foremost, if the Time Machine drives had been taken I would have been hosed. That was a single point of failure in my backup plan. In fairness, I use Arq to backup essentials like my iPhoto library and my source code, but there’s so much more that was not backed up.
What was covered:
- Dropbox had many essential documents. Many months ago I bought in and started keeping some essential data in my DB folder and have been slowly building up usage of this.
- iTunes Match had my music. A few clicks and I would have started to pull down just about everything (Apple or not).
- Arq/S3 had my photos and code. Again, a few clicks and this would have come down as well.
- BitBucket had my private code. I love that I get free private repos here. Take a look.
- Gmail had most of my mail. I moved all my old mail off my machines and into a Gmail account long ago so I could have search (back when Mail’s search was shit). Then I moved some mail off Gmail to a local mail server (running on the MBP) because I could. That almost resulted in the loss of ten years of mail, were it not for…
- Time Machine had full backups. This is how I ultimately recovered my data, but if I didn’t have it then the above would be the only data I got back.
What wasn’t covered:
- Everything not covered by the solutions above.
- An external drive with 2.5TB of data. It has a twin that holds a nightly mirror, but if both were taken I would have lost home movies, lots of old documents, my virtual machines, my server backups (rsync), and many years of WWDC videos and materials (can be reacquired … very slowly).
Change of Plan
Time Machine saved me, so it stays around.
The new plan is that now — in addition to local Time Machine backups — I’m adding 100% offsite coverage on backups.
I looked at Backblaze, CrashPlan, Mozy, and Carbonite and was really not taken by any of their solutions.
- Mozy started off as unlimited, years ago, and backtracked to storing 50-125GB of data. Recovery used to be by shipping physical media around, but it looks like they recently added “streaming restores” (ie. you can download your files now). I have more than 125GB of data.
- Carbonite looks like a winner, overall, except I have a Mac. The plan that I need, the one that supports external drives, isn’t available in the Mac software. Sorry you don’t want my money.
- CrashPlan is a Java app. Right out of the door I’m going to say no to that. That said, I’ve read good things about them from others and they are generally well-received, but they’re offering unlimited storage and have no idea what kind of a data hoarder I am. I fear they — and other backup providers — will eventually do what Mozy did and back off that promise.
- Backblaze shows great promise but lacks an in-place download feature. You can download a ZIP of some files or order (and pay more for) a thumb drive or hard drive of your data ($99/53GB or $189/3TB, respectively). While a good option for a total loss, it’s not my idea of perfect (“restore my old stuff in-place”). I did try it, just for kicks, and quickly learned that there’s a data file called bzfileids.dat that contains a mapping of file path to UUID on their server. This file cannot exceed 1GB in size and they’ve promised a fix for years, it seems. I have 4M files and 3TB of data to backup. It exceeded 1GB. I cancelled my account. It might be useful for web-and-email users, as long as you don’t have a lot of email (I have 20GB over 15 years, which is probably most of those 4M files).
I chose Arq again for my principal offsite backup. Arq supports both Amazon S3 and Amazon Glacier and those seem like the perfect solution for storing tons of data like this, so I’ll begin that backup soon (which will take weeks). The large data that will never change goes to Glacier; the day-to-day data goes to S3. I’ll need to clean out and organize my data before I start this, but that’s what this week is all about. I know this solution works, I know there are tools out there to get the data out of the archives without Arq being involved, should it die. I know I can order a copy of my data on a disk from Amazon if I need to and then use those tools to copy the data off, as well.
Cleaning out? What?
Well, I had two computers. The plan this year was to sell everything and consolidate to just … a MacBook Pro and a Thunderbolt Display.
(pause for effect)
With that so handily taken care of (ignoring the extremely private data loss and insurance deductible), I merged the two Time Machine backups on MBP and now have 400GB of data to sort through, much of it duplicate or outdated data.
Enter Hazel
Hazel is a must-have and has saved me a tremendous amount of time in this task so far. I created a folder that Hazel watched and then setup a ton of rules on how I wanted the files put in there sorted and Hazel just did it. It did it so well that I eventually just dumped most of my data in the folder and came back to almost everything sorted how I wanted it. I made a few changes to the rules and I’ll tweak it some more, but now I have a veritable Sorting Hat for files. Some go to the folder that will become the root of the Glacier archive and others will get sent over to Documents (and sorted) and be a part of the S3 archive.
Hazel + Arq = Magic
However, there’s more that Hazel has allowed than just that. Now my Downloads folder is smart. When music, movies, or ePubs are downloaded, they’re added to iTunes. When provisioning profiles are downloaded, they’re added to Xcode. When archives are downloaded they’re unpacked and the original archive is filed away based on the source site. I’ve turned off the “open safe downloads” and watch folder features of most of my applications and just made Hazel rules for those.
Lesson: Back up everything you would horribly miss if you had to be without it for more than a week. Also, Hazel.
Security
I know better. That’s the most painful part of this. I know better than to have left my computer in the state it was in. I just felt that the chances of anything happening to me were slim. Then someone breaks into your apartment while you’re out of town and the rules change.
Encryption
FileVault 2 has been enabled on the new system and my Time Machine backups are encrypted as well. This is the same technology, fundamentally (Core Storage encrypted partitions), but there are some nuances that should be noted about how the keys are handled. For Time Machine, the decryption password is entered on every mount of the drive (most secure) or stored in the keychain (secure enough, but a single point of failure — your account password). For FileVault 2 the keys are stored on the recovery partition and encrypted with your account password. If you have a weak account password then anyone in possession of your system can brute-force the keys and then decrypt the drive. Use a good password.
Before turning FileVault 2 on, you should read more about FileVault 2 and some of the limitations it imposes (no more remote reboots — you must unlock the system at boot to get at the decryption keys). Also, be aware your Apple ID is a potential security hole as well (unset your Apple ID for all accounts to avoid this). Note that the filesystem and mechanism have been researched, are well-documented, and tools are available to mount FileVault 2 disks so your password is all that protects your data.
Speaking of Passwords
I bought in to 1Password. Having keychains on different machines that may or may not have had the password I needed, having multiple browsers with their own schemes to store passwords, and then having mobile devices with their own stores of passwords posed several problems.
First, I don’t know how well any of them are really keeping my passwords secure. Keychain is good, but Chrome and Firefox can sync your passwords between machines and how well is it handling that? File security, transport security, server and network security are all important here.
I could research them all and answer those questions but that doesn’t solve the problem of consistency. 1Password does.
I found some scripts to export the Keychain and browser password stores and import them into 1Password. I then cleared out the browser and keychain passwords for anything in 1Password and went on my merry way, syncing over Dropbox and life is good.
Two-factor Authentication
Yes, it’s annoying, but do it. As I reset all my passwords (all of them) I turned on two-factor authentication wherever I could. Thankfully, most places that do it have moved to using a standardized method called Time-based One-time Password Algorithm and both the Google Authenticator and Authy apps on the iPhone support snapping a QR-code and hooking in. Authy looks nicer.
Recovery
I didn’t recover my computers. In all honesty, no thief is going to respond to a reward-bait message on a login screen, but I didn’t even have that. I had Find My Mac installed but made a critical error in using it. I locked it first.
Don’t do that.
You have two options here. You can hope for recovery or you can protect your data. If you hope for recovery then tell FMM to send you the location when it appears again and do nothing else until you get that email. Then tell the police (you filed a report, right?).
If you want to protect your data, tell it to wipe the machine. If you have FileVault 2 enabled it’s as easy as forgetting the encryption keys to the disk and is done in under a second. For other disks, blowing away the filesystem is a good start, but I’m not sure how it proceeds after that.
Why these two methods? If the thief knows you have a remote in to the machine, he’s going to just disconnect it from the network and brute-force his way in, if that’s what he wants. If you show your hand, you’ve lost the machine. If you’re willing to write the machine off, then just trash the data.
Locking the machine is useful in exactly one case: you have a reward message on the login screen and you’ve lost the machine, not had it stolen.
Aftermath
So, here I am with a nice new setup, my data back, and my personal life exposed to someone out there who I hope cares so little that he’s wiped the machine already. Bittersweet, but I’ve learned a few lessons.
- Plan for a loss ahead of time and get the proper insurance coverage.
- Go for security over convenience if that’s a decision. If you can get both, do it (1Password).
- Backup locally and remotely. Everything.
- Get the appropriate software and services installed to erase or locate your devices (and know how to use them).
Footnotes